Introduction
As organizations grow and adopt multiple platforms, managing user identities and access control becomes critical to ensuring security and efficiency. GitHub Enterprise, a widely used platform for collaboration and software development, offers Managed User accounts to help enterprises maintain control over user management and access. Integrating these Managed User accounts with Microsoft Entra ID (formerly Azure AD) provides a seamless identity and access management solution, enabling single sign-on (SSO), improved security, and streamlined administration.
In this article, we will explore how to integrate GitHub Enterprise Managed User with Microsoft Entra ID. We will cover the necessary steps to configure both platforms, highlight the benefits of this integration, and demonstrate how it can enhance security, compliance, and productivity across your development teams.
Pre-Requests
- Microsoft Entra ID
To register an Enterprise application and configure SCIM provisioning in Microsoft Entra ID, you need at least one of the following roles:- Application Administrator
- Cloud Application Administrator
- Global Administrator
- GitHub Enterprise Managed User Subscription
To enable the SAML SSO, you need a user with owner role
Enterprise App Registration in Entra ID
Login to entra.microsoft.com
Go to Identity-> Enterprise Applications -> Click on a new application search for the application “GitHub Enterprise Managed User” and click on Create.

Click on Single Sign-on from the manage blade -> select SAML
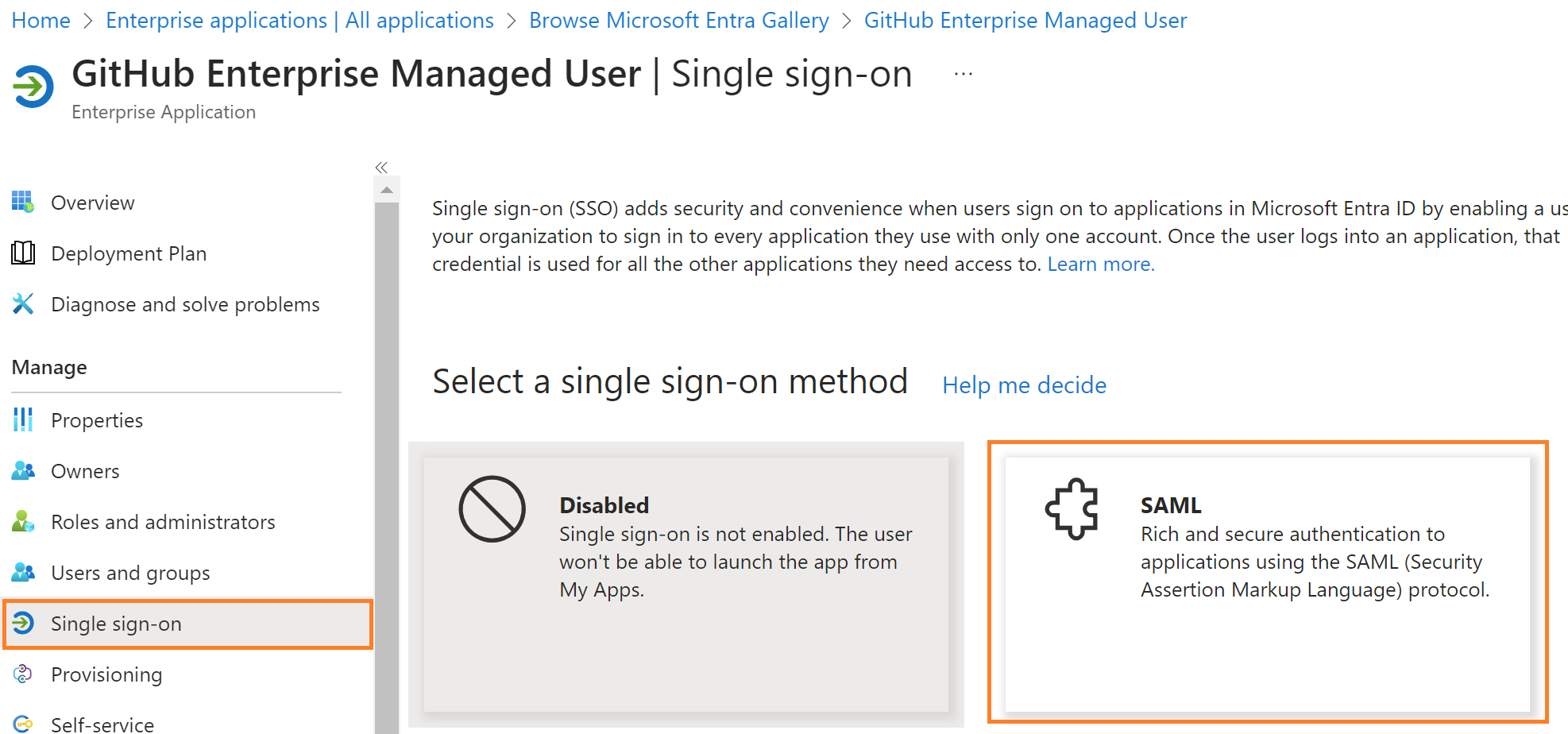
Edit Basic SAML Configuration
Identifier (Entity ID) – https://github.com/enterprises/{enterpise}
Note: Replace {enterprise Name} with your GitHub enterprise Name
Reply URL (Assertion Consumer Service URL) – https://github.com/enterprises/{enterprise}/saml/consume
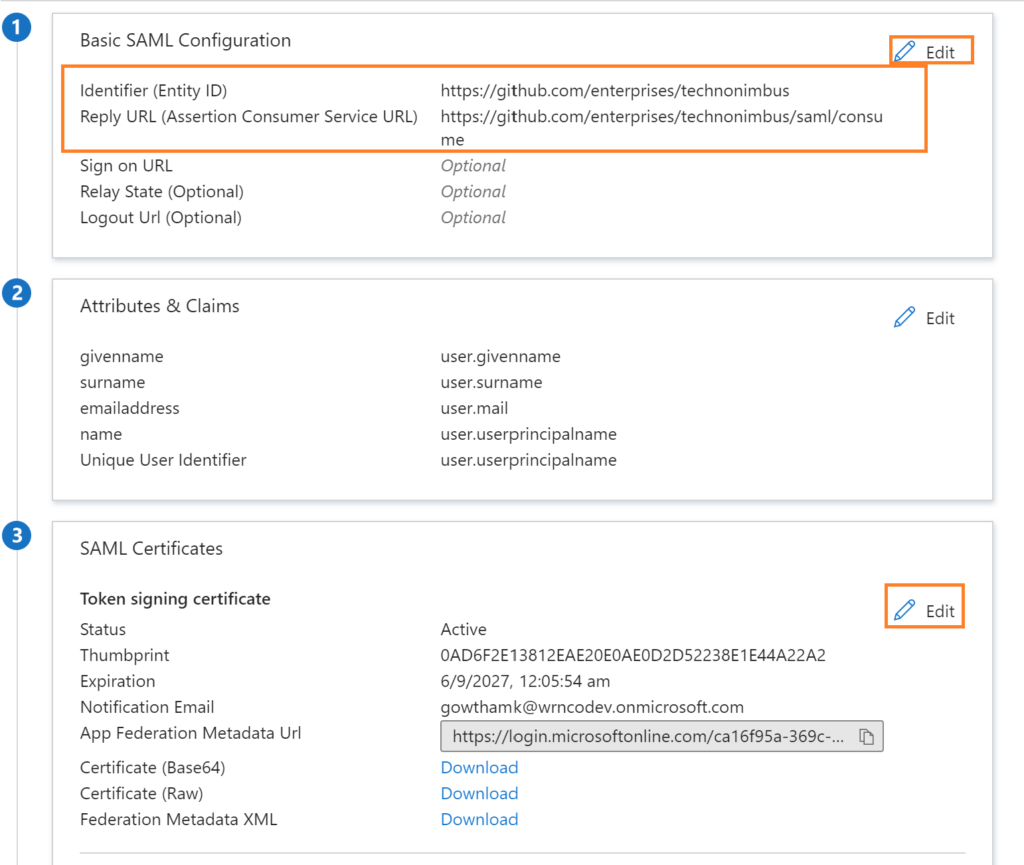
Download SAML Certificate
Download the PEM Certificate as shown in the figure below.
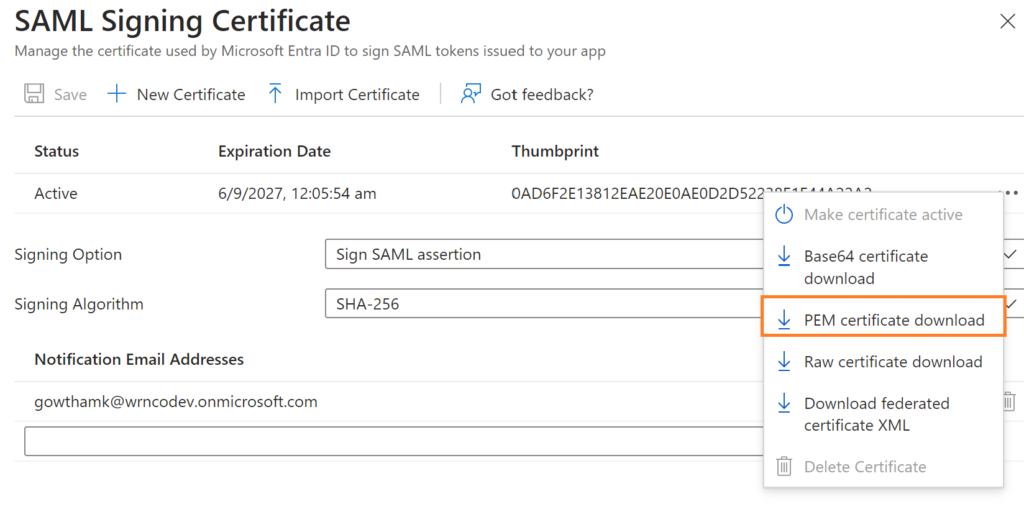
From Set up GitHub Enterprise Managed User section, copy the Login URL and Microsoft Entra Identifier, which we will use in the GitHub SAML Configuration.
Next, we want to configure a user assignment setting. Select properties from the application options, as shown in the below figure.
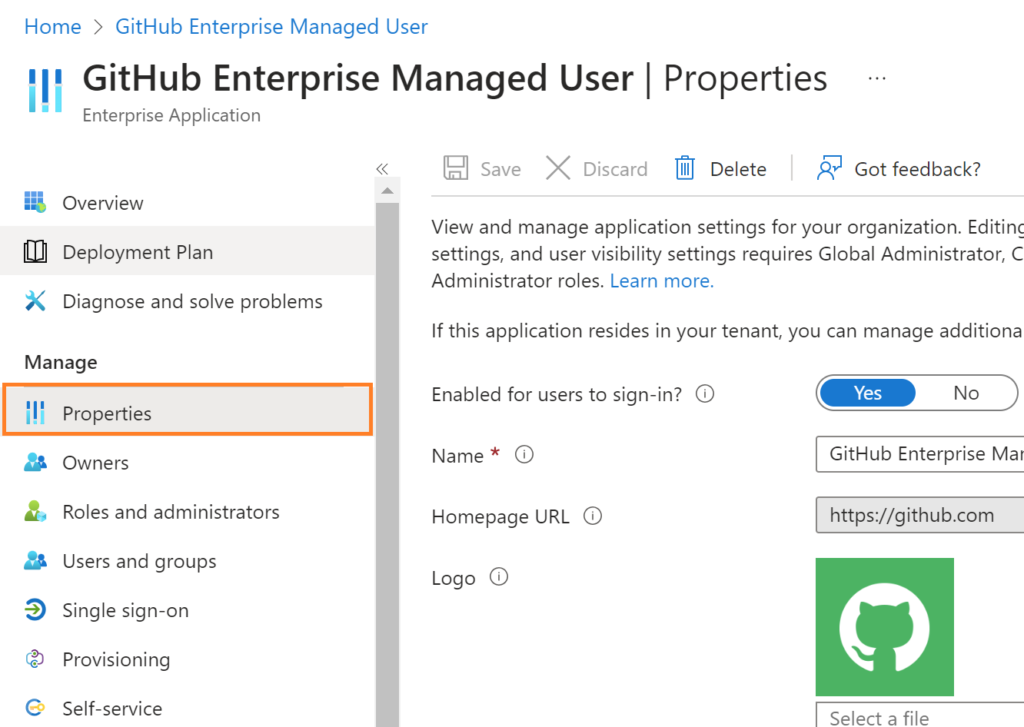
Set yes for Assignment required If you want to assign only a particular user or group to access the application, or set to no to provide access to all the users.
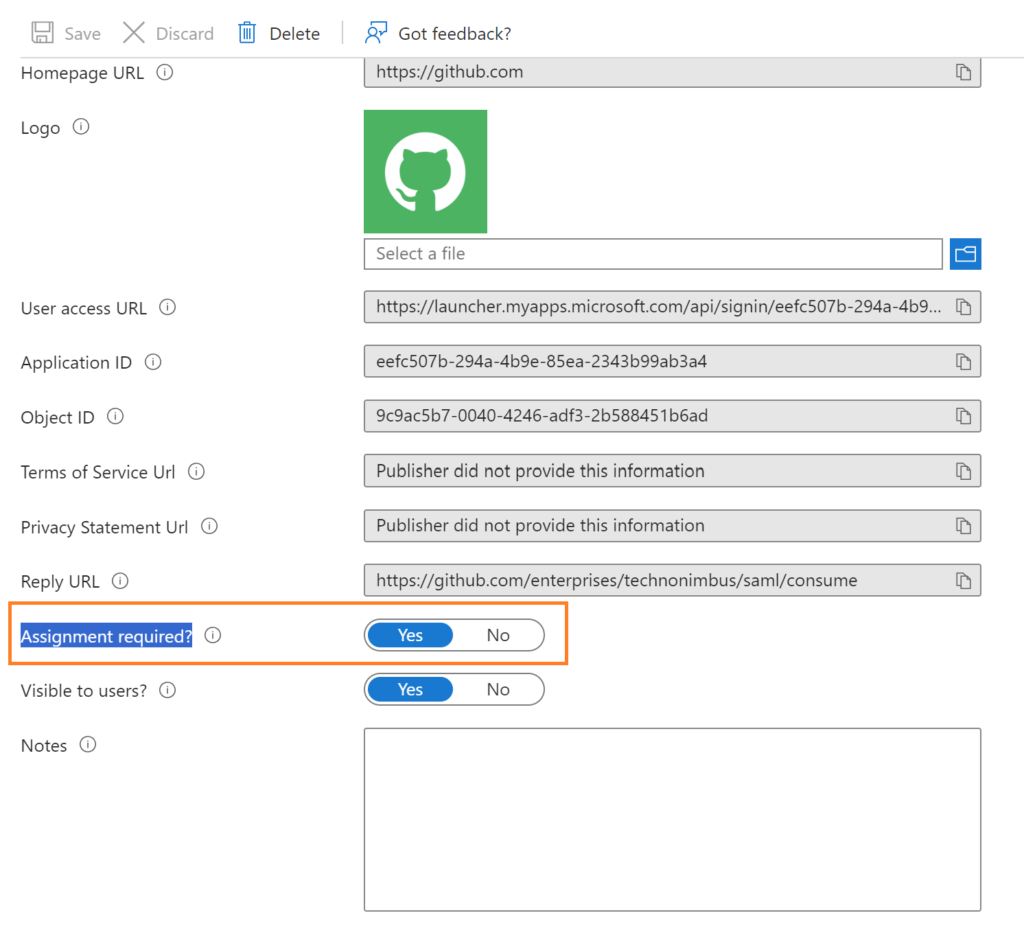
In my case I set to Yes for Assignment required, now select user and group and assign the group or user with respective roles to access the GitHub enterprise as shown in the below figure
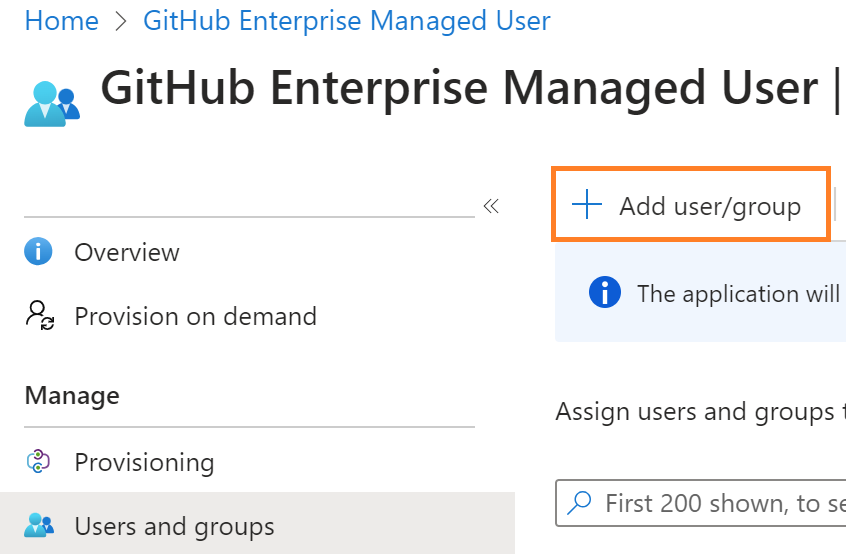
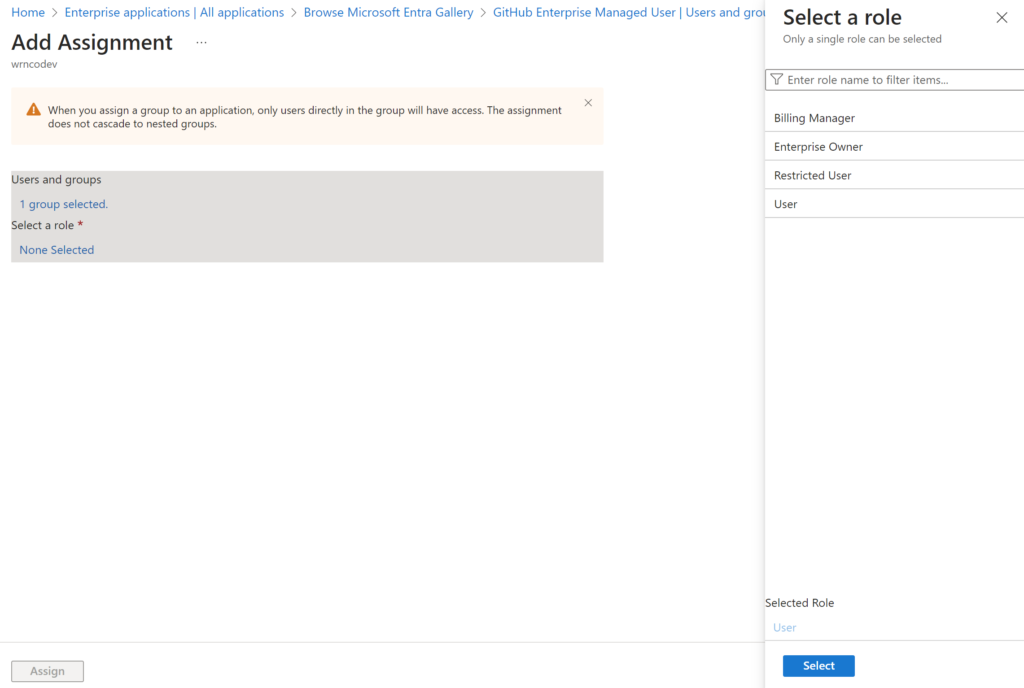
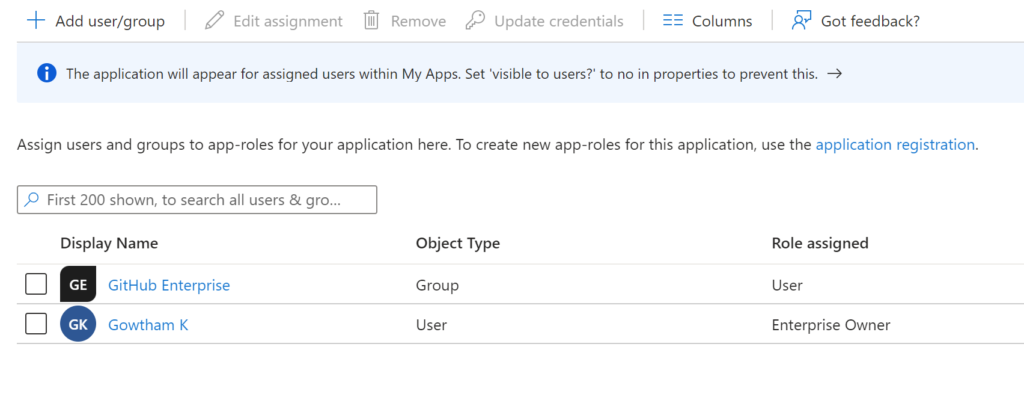
Make sure at least one user is assigned with Enterprise owners
Test the application
Select Single sign-on -> Test sign-in
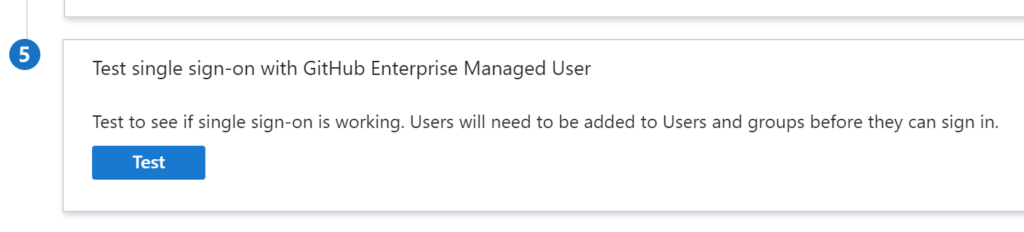
Enable SAML SSO in GitHub
Click on click on Profile -> Your Enterprise -> Settings – > Authentication security
Under SAML single sign-on
Enable Require SAML authentication
Paste the copied Login URL from the Entra ID GitHub application in place of Sign on URL field,
Paste the copied Microsoft Entra Identifier in place of the issuer field
Open the PEM certificate in Notepad, and copy and paste the content into the public certificate field
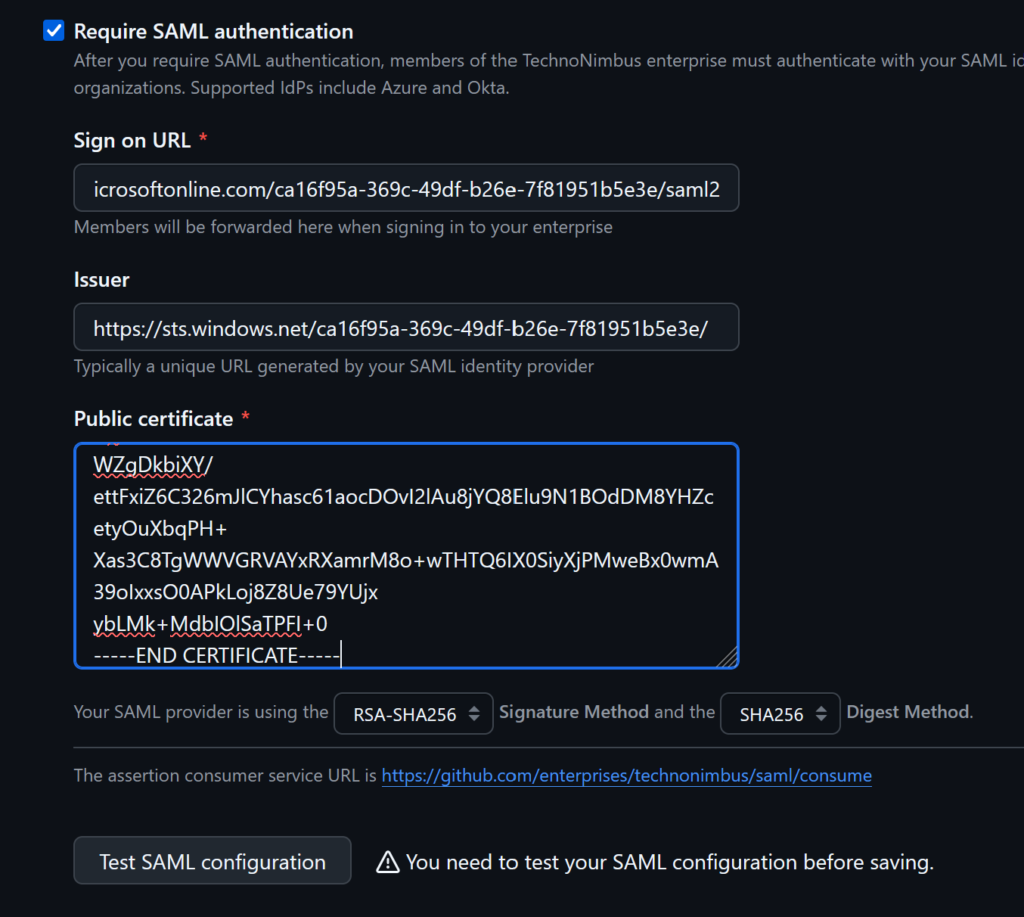
Test the SAML configuration
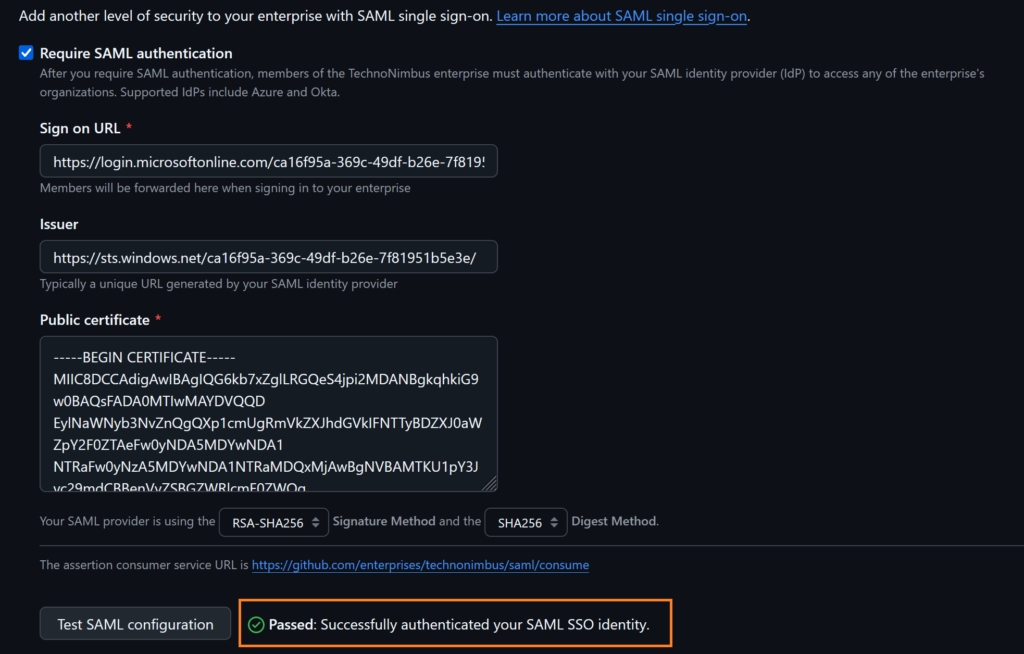
Once the test is passed save the SAML settings, make sure to download Single sign-on recovery codes, finally enable SAML Authentication, and click on continue
You will get the message “There was an issue joining the enterprise: Enterprise Managed Users must be provisioned via SCIM. Please reach out to your account manager for more information.”
Generate Personal Access Token
From the GitHub Enterprise, go to profile-> Setting -> Developer setting
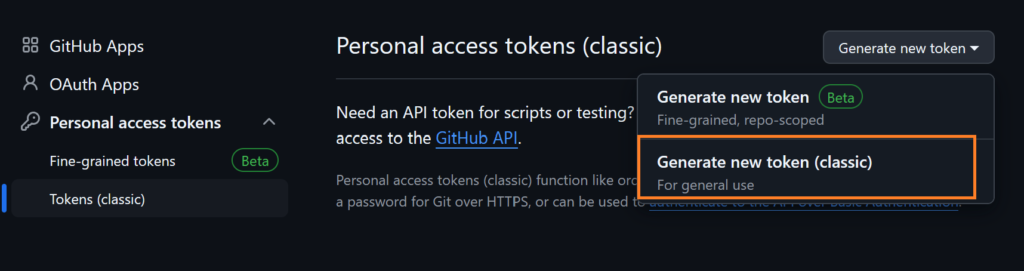
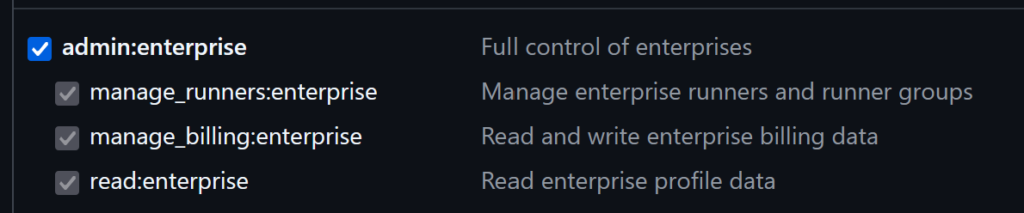
Select Tokens (classic) from Personal access tokens. Generate new token -> Generate new token (classic) Select admin:enterprise scope and click on the Generate token button
Copy the token
SCIM Provisioning
Select provisioning under the Manage section from GitHub Enterprise Managed User Enterprise application from Entra portal -> Click on the Get Started button, select automatic under Provisioning Mode
Under Admin Credential, select tenant URL
Tenant URL – https://api.github.com/scim/v2/enterprises/{enterprise}
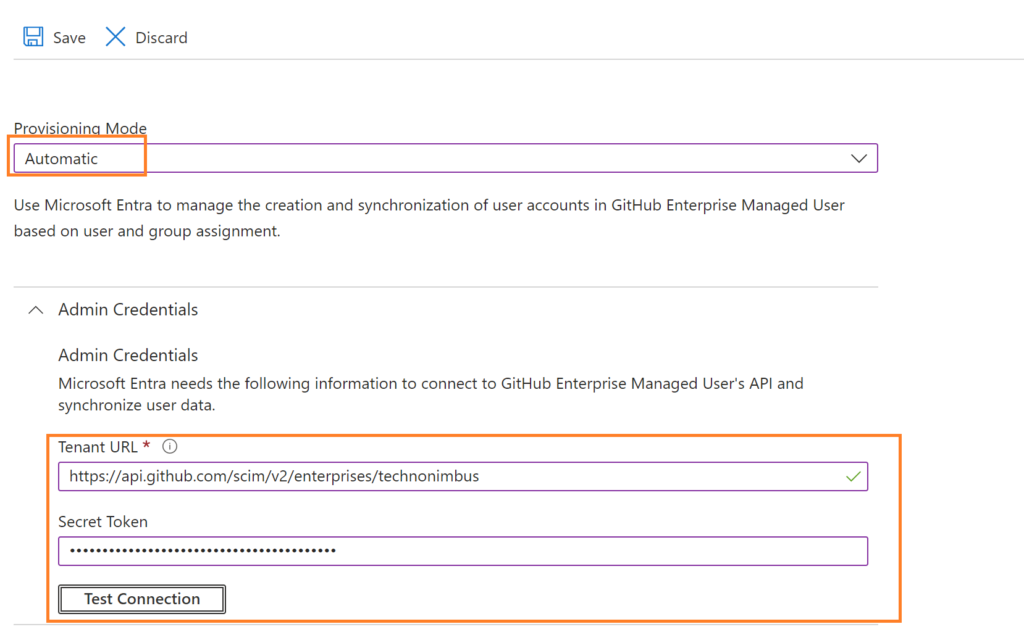
Paste the copied Personal access token in place of the secret token field
Click on the start provisioning button
You can check the status of the provisioning process as shown in the below figure
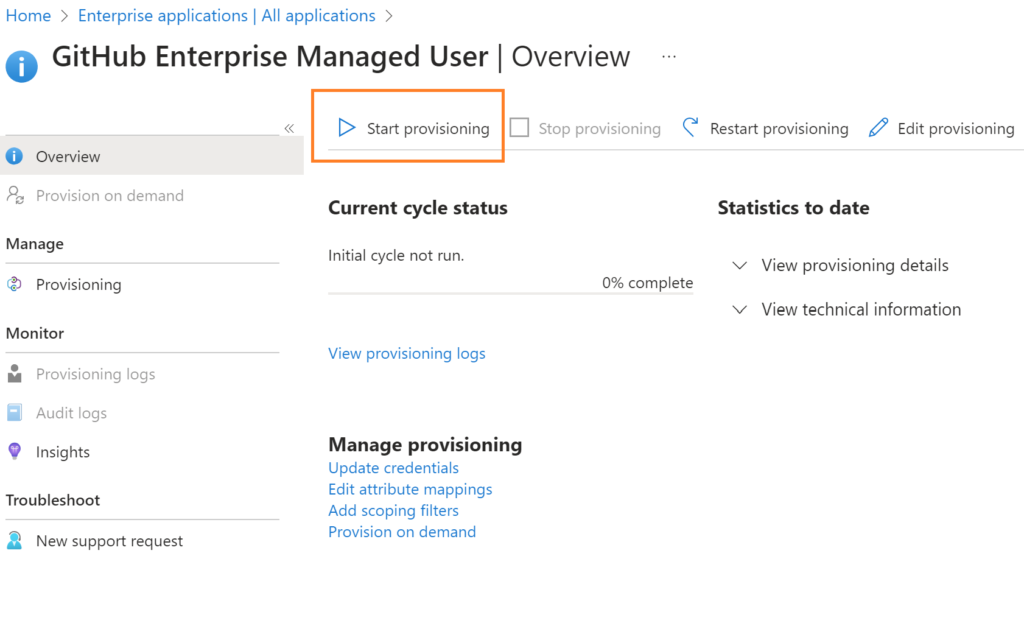
By default, the sync frequency is set to 40 mins.
Wait for some time to complete the sync process, once the sync completes you will get provisioning logs to track the user’s sync status.
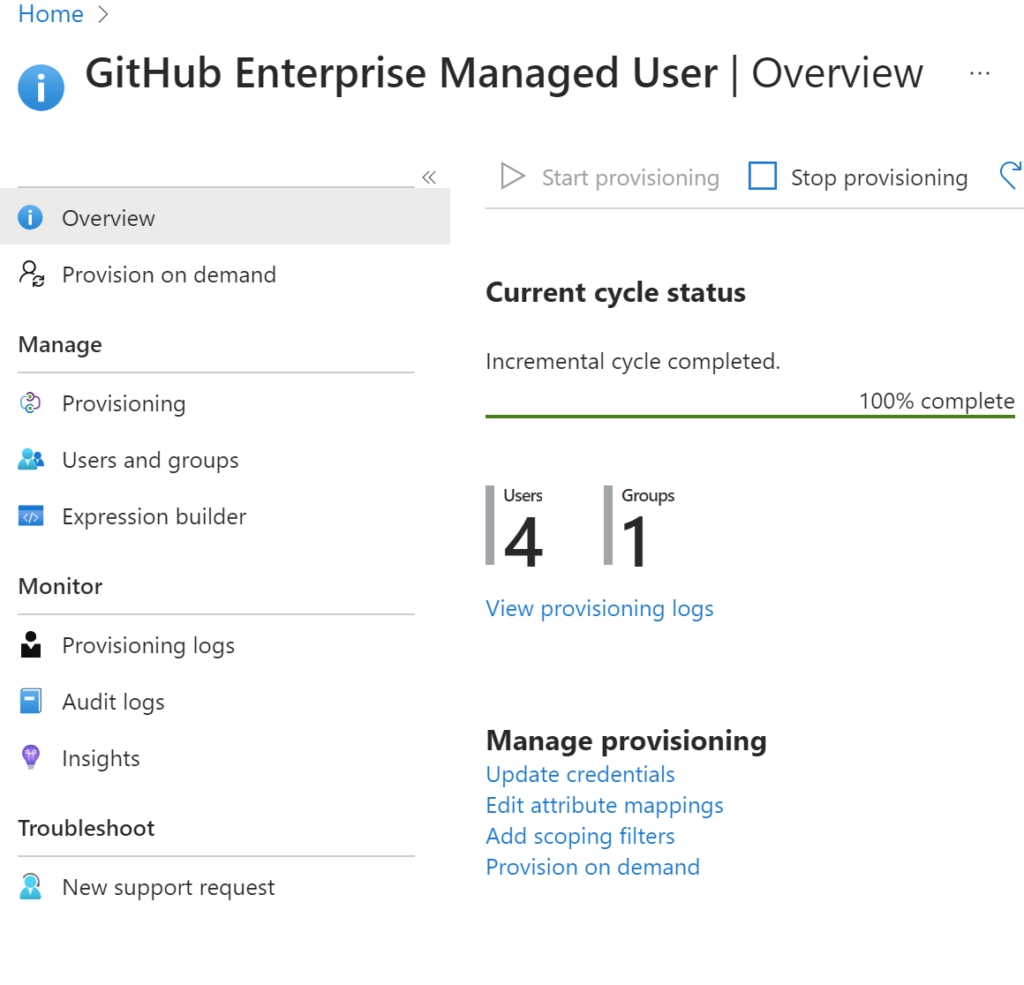
Our sync has been completed, you can see 4 users and 1 synced successfully.
Login to GitHub as admin to check the sync, from GitHub click on the profile and select your enterprise, go to identity provider -> Groups, you can find the group assigned to our GitHub Enterprise application in Entra ID is Synced with the GitHub directory using SCIM provisioning. Once the users are synced, the admin can manage the GitHub responsibilities.
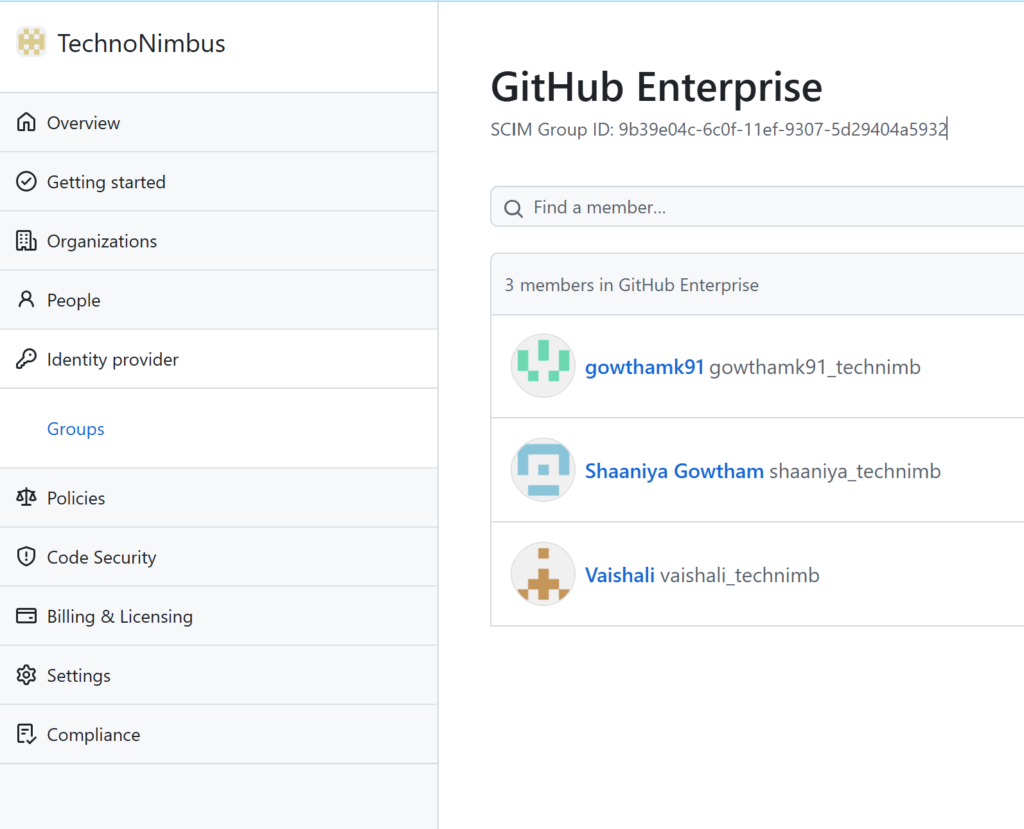
When you click on the group name it will display the list of users under that group. For a demo purpose, I just created a private repository called admin portal and I’m going to assign users (shaaniya_technimb and gowthamk_techmib) as a contributor.
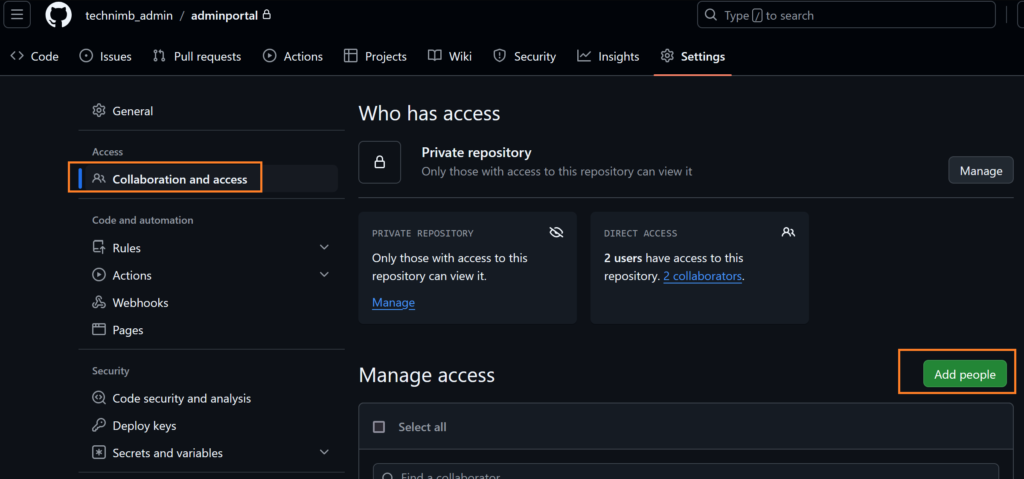
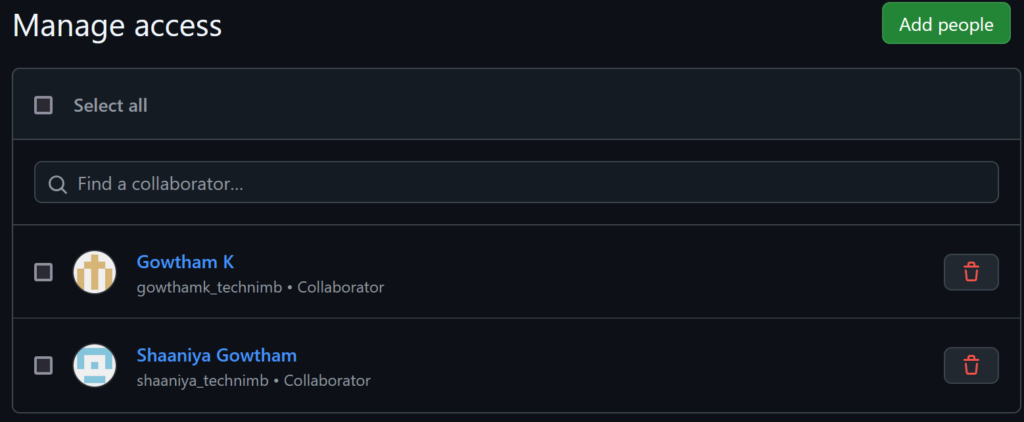
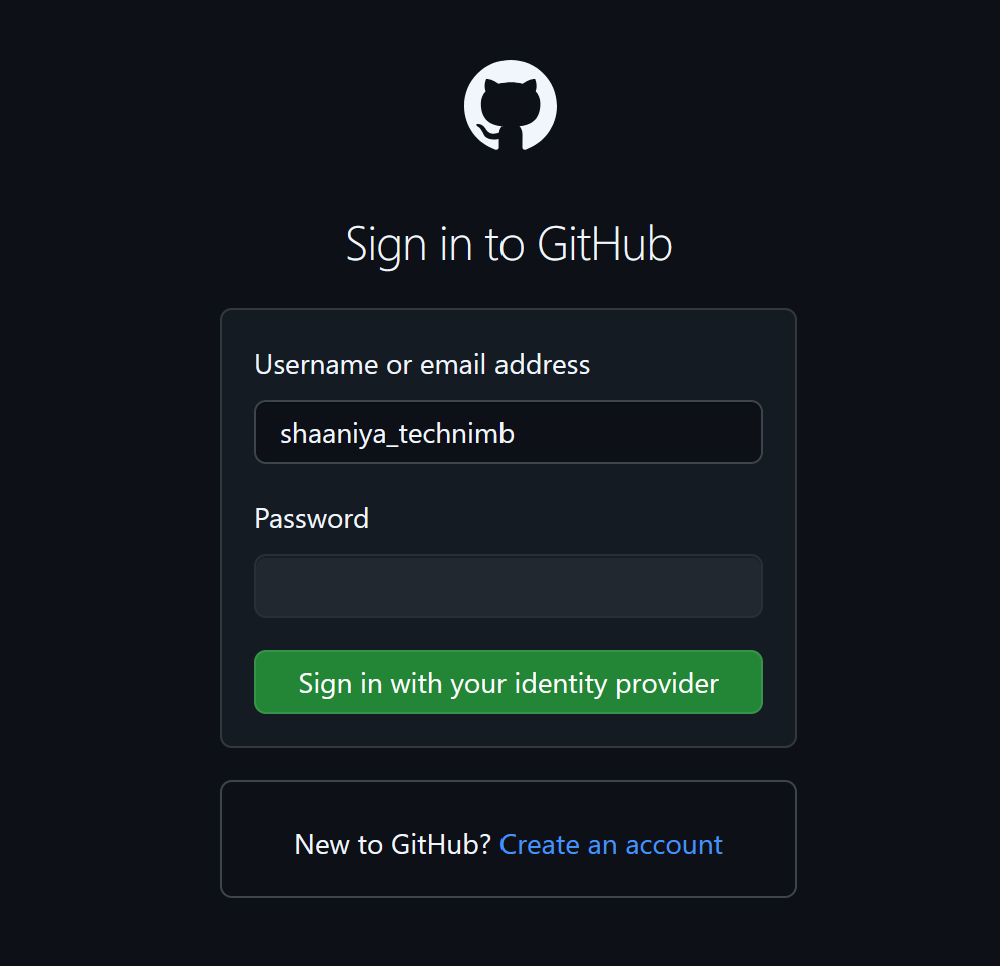
Now, open a new browser window, and let’s try to log in as a user(shaaniya_technimb)
GitHub will ask you to log in through IDP for SSO
Complete the login process through Microsoft login windows.
Now the user successfully landed into your GitHub Enterprise.
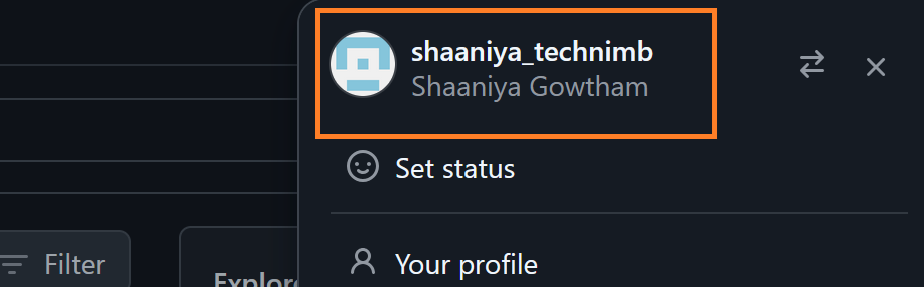
Check the repository access
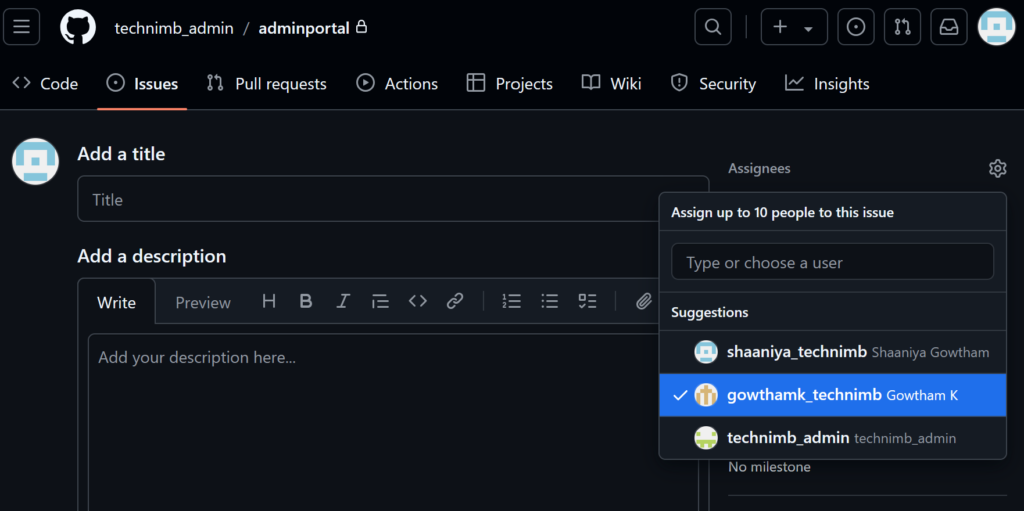
Now the user can create an issue, pull request, and other repository activities and assign it to other people as shown in the figure below.
Benefits of the Integration
- Centralized Identity Management
By integrating GitHub with Microsoft Entra ID, organizations can centralize their identity and access management, allowing IT administrators to manage user identities, permissions, and access to GitHub through a single, unified platform.
- Enhanced Security with SAML SSO
Implementing SAML-based Single Sign-On (SSO) strengthens security by enabling users to access GitHub with their Microsoft Entra credentials. This eliminates the need for multiple passwords and reduces the risk of credential-based attacks.
- Automated User Provisioning with SCIM
SCIM (System for Cross-domain Identity Management) automates the provisioning and de-provisioning of user accounts between Microsoft Entra ID and GitHub. This ensures that employee access to GitHub is automatically updated based on changes in the directory, saving administrative time and reducing human error. - Simplified User Lifecycle Management
The integration simplifies the process of managing user access, as users are automatically added or removed from GitHub based on their status in Microsoft Entra ID. This is especially beneficial for onboarding and offboarding employees, ensuring proper access control. - Improved Compliance and Auditing
The integration provides better visibility and control over user access to GitHub, making it easier for organizations to comply with security and privacy regulations. All access and changes are traceable, enabling effective auditing and reporting - Reduced Administrative Overhead
Centralizing authentication and user provisioning reduces the need for manual processes, lowering the risk of errors and reducing the workload for IT teams. Users can be managed in one place, cutting down the complexity of maintaining separate identity systems. - Seamless User Experience
Employees can use their familiar Entra ID credentials to access GitHub without needing to remember additional usernames or passwords, enhancing the overall user experience and productivity.
These benefits can lead to improved security, efficiency, and user experience for organizations managing development teams at scale.
Summary
This article provides a comprehensive guide on integrating GitHub Enterprise Managed User with Microsoft Entra ID to enable streamlined identity and access management across both platforms. The integration leverages SAML-based Single Sign-On (SSO) and SCIM provisioning to ensure seamless user management.
The article starts with an introduction to the key concepts of Microsoft Entra ID and GitHub Enterprise Managed User, followed by the necessary prerequisites for the integration process. It then walks through the detailed steps for registering the GitHub application within Entra ID, enabling SAML SSO in GitHub, and generating a Personal Access Token for API-based operations. The article concludes with configuring SCIM provisioning, which automates user provisioning and de-provisioning, ensuring that user data is synchronized between the two platforms.
References:
