Introduction:
Like Microsoft Entra ID, there is no Azure AD B2C user flows admin center to manage a particular user’s MFA. However, we can achieve it through the conditional access policy. We can set the MFA for the user flow on or off or define the conditional access policy. This document will educate you on configuring a conditional access policy for the user flow to bypass the MFA for a particular user.
Configure Conditional Access Policy:
Step 1: Login to Azure AD B2C tenant
Step 2: Go to Azure AD B2C -> Select Conditional Access under Security Blade
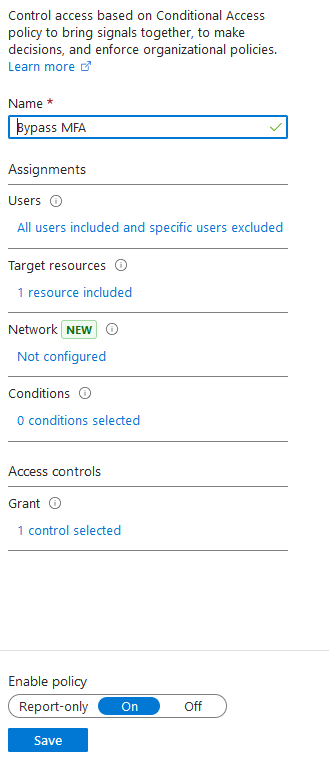
Step 3: Select New Policy and name the policy. I called it as “bypass MFA”.
Step 4: Under Assignments, select Users and select the user from the exclude section to bypass the MFA for that user and include all other users
Step 5: From Target resources, select the resources/cloud app where this policy should be applied
Step 6: Under access control, select Grant -> Grant access – select Require multifactor authentication.
Step 7: Apply conditional access policy to the user flow
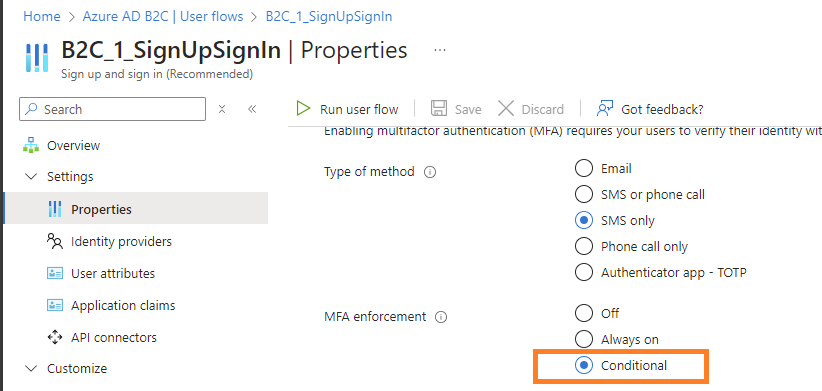
Step 8: Enforce conditional access policies

The Azure AD B2C conditional access policy has some limitations; please review the documents to determine these limitations.
Summary:
We have seen how to configure Azure AD B2C Conditional Access to bypass Multi-Factor Authentication (MFA) for individual users selectively. This guide provides step-by-step instructions for creating policies based on user attributes. Explore scenarios for user-specific MFA exemptions while maintaining security. This is ideal for developers managing diverse authentication needs in consumer applications.
